Project Overview
Comprehensive documentation of the Lightweight Webtraffic Inspection Tool; including abstract, objectives, methodology, technologies used, obtained results, and planned future enhancements.
Abstract
The HTTPS protocol's widespread use has significantly increased the amount of traffic on the encrypted network, enhancing user privacy while also decreasing visibility for administrators who need to identify security risks within encrypted channels. While advanced TLS inspection appliances are necessary for large enterprises, smaller organizations rarely have access to such solutions due to their financial and technical limitations. Creating a security gap where malware, suspicious domains, and harmful file downloads can slip past traditional monitoring tools without being noticed. To close this gap, this project develops a lightweight modular TLS Inspection Proxy that makes it easier and more accessible to selectively and transparently inspect HTTPS flows. The system makes use of the mitmproxy framework, which is improved with custom Python add-ons for metadata extraction, domain and file filtering, and automated file hashing for larger files. It uses the VirusTotal API to analyze suspicious files to detect malicious content in real time. All activity is logged in a structured SQLite database, documenting client–server metadata and inspection results. For effective traffic monitoring, a Flask web dashboard shows system activity. Testing verified efficient TLS traffic interception and filtering without major performance problems, making this solution more affordable, deployable, and transparent than other approaches. It shows how a lightweight inspection mechanism can enhance visibility and support early threat identification in encrypted traffic environments, catering to small networks.
Objectives
Minimal Configuration & Ease of Use
Build an easy-to-use TLS inspection environment that requires minimal configuration and technical background.
Automated Threat Verification
Hash downloaded files (e.g., SHA-256) and verify them automatically using services like VirusTotal.
Intelligent Traffic Filtering
Use text-based rules to block suspicious domains and file extensions.
Comprehensive Real-Time Logging
Store inspected HTTPS flows in a searchable database for clear visibility into past activities.
Intuitive Monitoring Dashboard
Provide a web dashboard that displays traffic, alerts, and hash results in real time.
Optimized Performance & Security
Ensure the inspection process is accurate, secure, and performs with minimal overhead.
Methodology & System Architecture
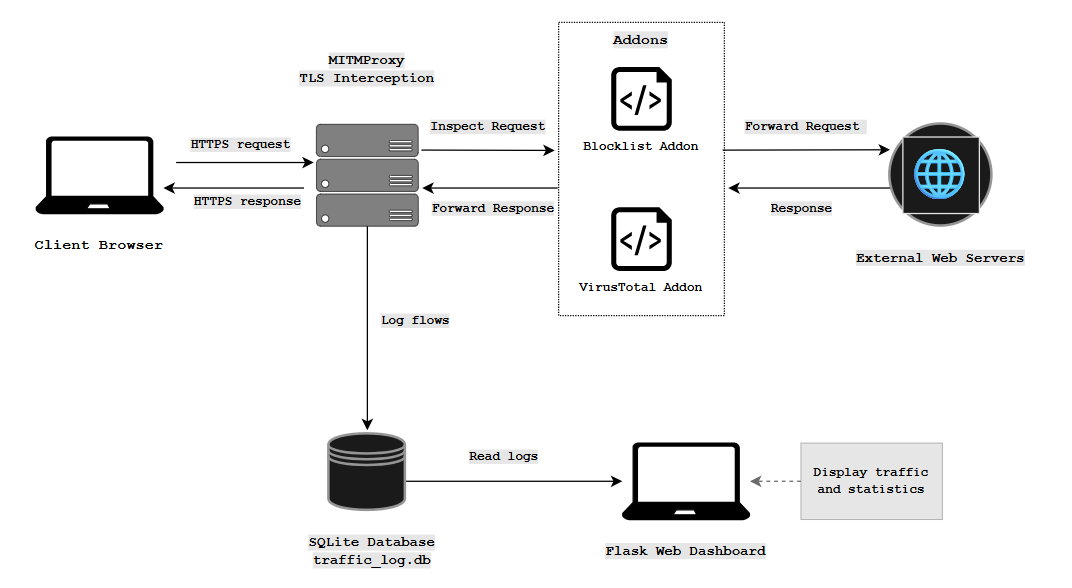
The system's architecture uses a Middle Agent model, with mitmproxy at its core to transparently intercept and decrypt HTTPS traffic. The data flow starts with a client request being captured and decrypted. A custom Python add-on then inspects the request, checking it against blocklists for domains, URLs, and file extensions.
If the request is safe, it is forwarded to the web server. The server's response is then intercepted again and passed to a second add-on that leverages the VirusTotal API to scan for malicious content. Based on the result, the response is either sent back to the client or blocked. For full transparency, all traffic and decisions are logged in a central SQLite database, which powers a Flask web dashboard for real-time monitoring and visualization.
Technologies Used
Core Programming
- Python 3
- HTML5 / CSS3
- SQL
- JavaScript (ES6+)
- Bash Shell commands
Key Tools & Frameworks
- mitmproxy (traffic interception & inspection)
- Python Virtual Environment
- VirusTotal Public API
- Flask (web dashboard)
- SQLite (event logging & storage)
Results & Implementation
- Successfully intercepted, decrypted, and inspected HTTPS traffic using a lightweight web traffic proxy setup.
- Implemented custom add-ons for domain blocking, extension filtering, and automated file hashing.
- Integrated VirusTotal API to detect and block malicious or suspicious downloaded files in real time.
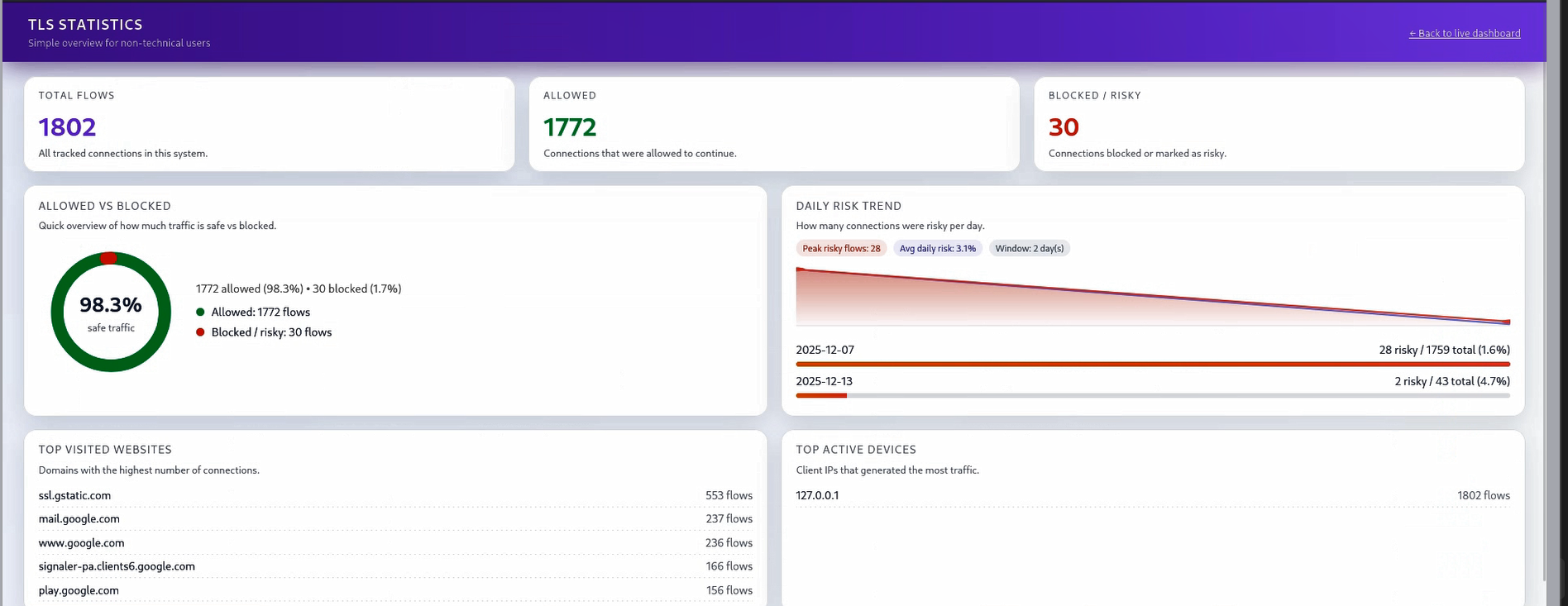
- Stored all traffic logs—including URLs, IPs, timestamps, and block actions—securely in an SQLite database.
- Developed a user-friendly Flask dashboard to visualize traffic, display flow details, and track blocked threats.
- Demonstrated a simplified configuration process that makes TLS inspection accessible to non-expert users.

Conclusion & Future Work
The developed solution achieves its core objectives of providing accessible TLS traffic inspection and policy enforcement. Planned future work includes:
- Implement advanced hashing methods (e.g., deep hashing) to improve detection of modified or partially similar malicious files.
- Integrate real-time threat intelligence feeds to instantly detect malicious domains, IPs, and URLs.
- Implement real-time alerts for suspicious activity via email, SMS, or dashboard notifications.
- Add user authentication to secure access to the dashboard.
- Integrate machine learning models to automatically detect anomalous patterns and identify malicious HTTPS flows.
- Enable traffic inspection from remote devices and cloud deployments for centralized monitoring.
